FTPS 分为2种,Implicit 和 Explicit,即隐式和显示,Passive 模式下的 Implicit FTPS 默认监听 990 端口(控制信号端口),传输的数据端口与服务器协商,另行发起一个数据传输端口,也就是会创建 2 个连接端口,Active 模式下的 Implicit FTPS 使用的数据通道是 989,控制端口还是 990。
隐式 FTPS 的 990 端口是约定俗成预定义的,服务端和客户端会同时自动通过 TCP 990 端口加密传输控制信号,989 用于数据传输,TCP 三次握手之后,从初始化连接开始的数据就已经完全加密的。
Explicit FTPS 初始阶段安全性差,开始时会发送明文 Auth 指令请求服务端加密,而 FTPS 服务端完全可以控制是否要加密,也就是实际上的实现有 2 种,21 端口用于控制信号传输,发送 Auth,服务端响应 Auth 加密请求,接下来的控制信号和身份验证全部加密,或者拒绝,接下来的控制信号端口和数据端口仍然是明文的,此外,Explicit FTPS 的一般默认只保护信号通道,数据通道可选保护,具体看客户端和服务端 FTPS 协商结果,也就是 Explicit 存在完全可以是全部明文传输的可能。
这个在我看来完全是杜撰出来的说法,老外想着允许降级并不是强制实施的显示 FTPS,足够灵活,但这种既然已经指明明确用于 FTPS 安全加密传输的场景,怎么会去考虑降级?服务端不支持 FTPS,应直接抛出异常拒绝连接,要用明文,你倒是别用 安全加密的传输端口,用回 20、21 端口不就得了,哪来的兼容问题,现在 https 网站不支持,谁会给你跳80?会给你在 443 端口 通讯 80 端口的明文内容?哪家浏览器、web 服务端会允许?不支持就断开连接,没有后退协商余地的,必须是支持https的浏览器客户端。
隐式 FTPS 被 IETF 弃用了,详见 http://www.ford-hutchinson.com/~fh-1-pfh/ftps-ext.html#bad ,并最终在草案阶段被淘汰,有且只有一种 Explicit,且最终通过了 RFC 2228 、RFC 4217 进行了标准化,下面附上原文
ftps - an overview
Interoperating ftp and ssl has been defined in three ways.
According to the current internet draft specification (draft-murray-auth-ftp-tls-16.txt) only one of them is now considered valid.
They are:
"SSL connect"
Connect to a separate port (defined by IANA to be 990) and perform SSL negotiation. The default data port (U-1 -> 989) also has implicit SSL protection. THIS IS BAD why ?
"AUTH SSL"
Connect as usual to port 21 and use "AUTH SSL" or "AUTH TLS-P" to ask for SSL negotiation and implicitly protect further data connections. THIS IS BAD why ? (There is also a compatibility problem here, in that Tim Hudson's original code gave a '334' reply to AUTH SSL - this is now considered harmful and '234' should be used. Clients are OK because they can accept both - but there still exist some broken servers which send '334')
"AUTH TLS"
Connect as usual to port 21 and use "AUTH TLS" or "AUTH TLS-C" to ask for SSL negotiation without implicitly protecting the data connection (this is achieved with the "PROT P" command) THIS IS GOOD
Why are they bad ?
From draft-murray-auth-ftp-ssl-07.txt
A. Deprecated SSL negotiation mechanisms
There are two other mechanisms that have been used for FTP over SSL,
these mechanisms do not conform to [RFC-2228] and so are now
deprecated. They are documented below.
i) Implicit SSL protection of the FTP session
There is a port, registered with the IANA, for secure FTP using
ssl {FTP-TLSPORT}. This approach can be likened to the [RFC-2818]
approach for https, in that the SSL negotiation happens upon
connection (for the control and all data connections). This
approach is not favoured by the IETF and should not be used for
new FTP-TLS implementations.
ii) Protection using the 'AUTH SSL' command
Early implementations of the negotiated SSL upgrade, using the
AUTH command implemented it in a slightly different way that that
used in this document.
The parameter on the the AUTH command is 'SSL' and not 'TLS' and,
once the control connection is secured, the state of the data
connection is implicitly secure. This approach is in direct
disagreement with [RFC-2228] which requires the PROT command to be
issued and so should not be used in new implementations
As a historical note, very early implementation of this approach
issued and expected a '334' reply from the 'AUTH SSL' command.
This should be contrasted to the '234' reply defined in this
document.
SFTP 是基于 SSH 的扩展,完全 2 个东西,这里不做赘述。
为了安全,我这里启用 Implicit FTPS,这个必须要 Pure-FTPd 编译时加入如下参数,不然是不支持的,同时防火墙需要放行 TCP 989/990 端口,这样就能从 TCP 3 次握手连接建立就实现命令通道和数据通道全程加密!
到这里下载重新编译,GitHub传送门:https://github.com/jedisct1/pure-ftpd/releases
--with-implicittls
我这里加上这个参数后,全部编译参数如下
--with-tls --with-certfile=/etc/ssl/private/pure-ftpd.pem --with-cookie --with-diraliases --with-everything --with-ftpwho --with-language=english --with-peruserlimits --with-puredb --with-quotas --with-ratios --with-sysquotas --with-throttling --with-uploadscript --with-virtualchroot --with-virtualhosts --with-boring --with-bonjour --with-rfc2640 --with-implicittls
接下来停止原来的 Pure-FTPd 进程,,默认编译完是安装到 /usr/local/sbin/pure-ftpd这里,直接把二进制文件替换到你原先的安装位置覆盖即可。
那些上古时代的客户端就不要使用了,比如 Flashxp,最新版的最后更新时间是 2013 年,实测发现 FTPS 协商时的 TLS 版本只能达到 TLS v1.0(太旧没更新),直接与FTP服务端协商失败,因为服务端的 OpenSSL 不支持虚弱密码套件,要求 TLSv1.1+,推荐使用开源的 FileZilla ,更新勤快,跨平台客户端、服务端,完美按照 RFC 规范实现,无兼容和各种奇奇怪怪的问题。
安卓端 实测 ES 文件浏览器 v4.2.6.7/MiXplorer v6.56.5 内置的ftp添加挂载,Implicit FTPS全部成功。
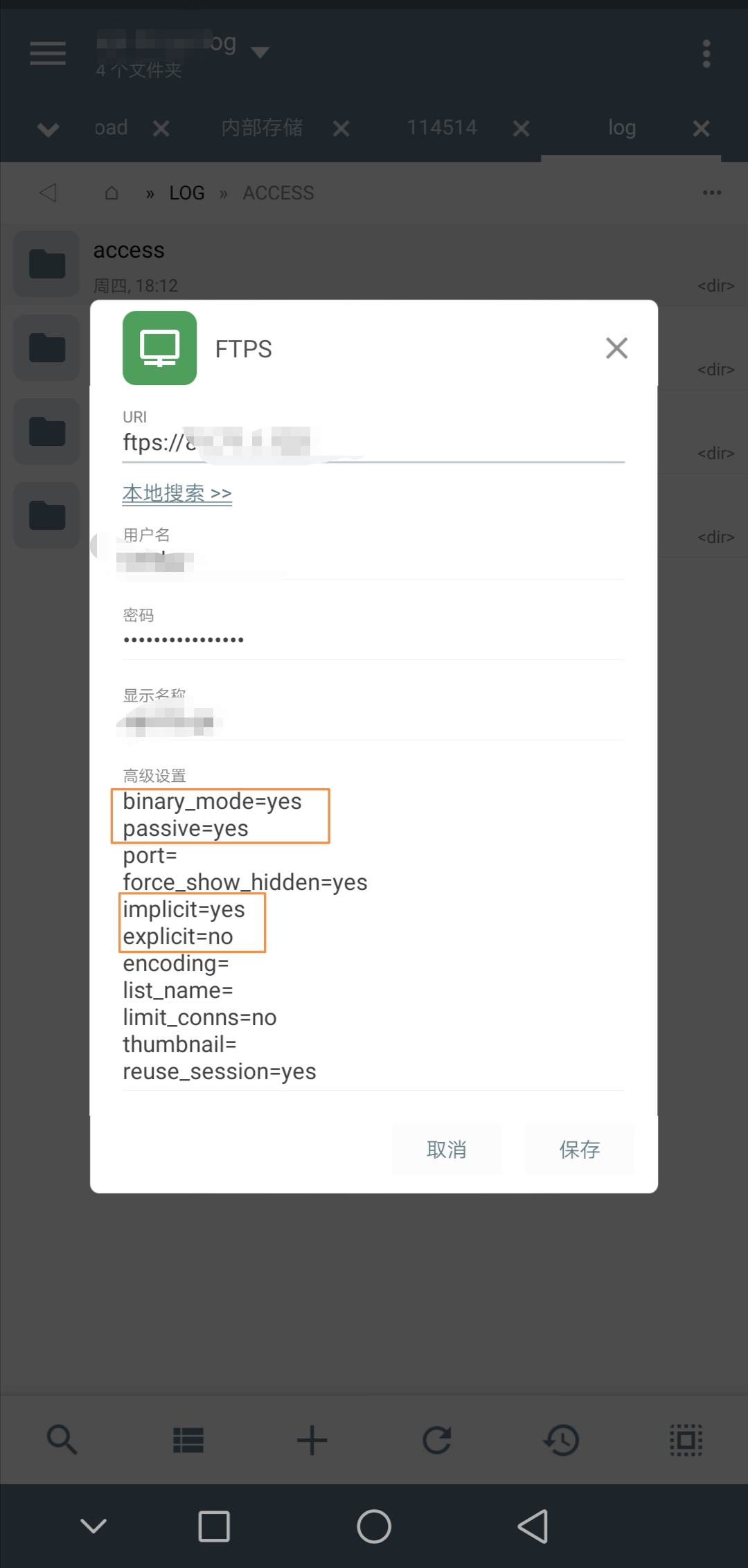
这里有个坑,Pure-FTPd 服务端,启用 Implicit 编译参数,就不支持显示 Explicit FTPS 了,详见 GitHub 项目说明。
关于那个 SSL 协商有几个注意的,Pure-FTPd 采用的 SSL/TLS 协议安全强度,取决于编译时本机的 OpenSSL 版本,在CentOS 7.x 系统上,默认自带的为 1.0.2k-fips 26 Jan 2017, 使用 openssl ciphers -v检测支持的加密算法,发现RC4、SSLv3、3DES、CAMELLIA256、IDEA等虚弱过时加密算法赫然在列,到低版本的 OpenSSL 系统上抓取协商信息,我直呼好家伙,居然使用SSLv3建立的加密连接,醉了,手机端是 MiXplorer 是很新的版本了(v6.56.5-Silver Build 2021-06-05),服务端(不是FTP服务端)和客户端一起背锅,支持弱密码套件的服务端 OpenSSL,只支持虚弱不安全协议的 FTPS 客户端。
OpenSSL 输入 openssl ciphers -v 检测支持加密算法,返回如下信息:
ECDHE-RSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH Au=RSA Enc=AESGCM(256) Mac=AEAD
ECDHE-ECDSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESGCM(256) Mac=AEAD
ECDHE-RSA-AES256-SHA384 TLSv1.2 Kx=ECDH Au=RSA Enc=AES(256) Mac=SHA384
ECDHE-ECDSA-AES256-SHA384 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AES(256) Mac=SHA384
ECDHE-RSA-AES256-SHA SSLv3 Kx=ECDH Au=RSA Enc=AES(256) Mac=SHA1
ECDHE-ECDSA-AES256-SHA SSLv3 Kx=ECDH Au=ECDSA Enc=AES(256) Mac=SHA1
DH-DSS-AES256-GCM-SHA384 TLSv1.2 Kx=DH/DSS Au=DH Enc=AESGCM(256) Mac=AEAD
DHE-DSS-AES256-GCM-SHA384 TLSv1.2 Kx=DH Au=DSS Enc=AESGCM(256) Mac=AEAD
DH-RSA-AES256-GCM-SHA384 TLSv1.2 Kx=DH/RSA Au=DH Enc=AESGCM(256) Mac=AEAD
DHE-RSA-AES256-GCM-SHA384 TLSv1.2 Kx=DH Au=RSA Enc=AESGCM(256) Mac=AEAD
DHE-RSA-AES256-SHA256 TLSv1.2 Kx=DH Au=RSA Enc=AES(256) Mac=SHA256
DHE-DSS-AES256-SHA256 TLSv1.2 Kx=DH Au=DSS Enc=AES(256) Mac=SHA256
DH-RSA-AES256-SHA256 TLSv1.2 Kx=DH/RSA Au=DH Enc=AES(256) Mac=SHA256
DH-DSS-AES256-SHA256 TLSv1.2 Kx=DH/DSS Au=DH Enc=AES(256) Mac=SHA256
DHE-RSA-AES256-SHA SSLv3 Kx=DH Au=RSA Enc=AES(256) Mac=SHA1
DHE-DSS-AES256-SHA SSLv3 Kx=DH Au=DSS Enc=AES(256) Mac=SHA1
DH-RSA-AES256-SHA SSLv3 Kx=DH/RSA Au=DH Enc=AES(256) Mac=SHA1
DH-DSS-AES256-SHA SSLv3 Kx=DH/DSS Au=DH Enc=AES(256) Mac=SHA1
DHE-RSA-CAMELLIA256-SHA SSLv3 Kx=DH Au=RSA Enc=Camellia(256) Mac=SHA1
DHE-DSS-CAMELLIA256-SHA SSLv3 Kx=DH Au=DSS Enc=Camellia(256) Mac=SHA1
DH-RSA-CAMELLIA256-SHA SSLv3 Kx=DH/RSA Au=DH Enc=Camellia(256) Mac=SHA1
DH-DSS-CAMELLIA256-SHA SSLv3 Kx=DH/DSS Au=DH Enc=Camellia(256) Mac=SHA1
ECDH-RSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH/RSA Au=ECDH Enc=AESGCM(256) Mac=AEAD
ECDH-ECDSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH/ECDSA Au=ECDH Enc=AESGCM(256) Mac=AEAD
ECDH-RSA-AES256-SHA384 TLSv1.2 Kx=ECDH/RSA Au=ECDH Enc=AES(256) Mac=SHA384
ECDH-ECDSA-AES256-SHA384 TLSv1.2 Kx=ECDH/ECDSA Au=ECDH Enc=AES(256) Mac=SHA384
ECDH-RSA-AES256-SHA SSLv3 Kx=ECDH/RSA Au=ECDH Enc=AES(256) Mac=SHA1
ECDH-ECDSA-AES256-SHA SSLv3 Kx=ECDH/ECDSA Au=ECDH Enc=AES(256) Mac=SHA1
AES256-GCM-SHA384 TLSv1.2 Kx=RSA Au=RSA Enc=AESGCM(256) Mac=AEAD
AES256-SHA256 TLSv1.2 Kx=RSA Au=RSA Enc=AES(256) Mac=SHA256
AES256-SHA SSLv3 Kx=RSA Au=RSA Enc=AES(256) Mac=SHA1
CAMELLIA256-SHA SSLv3 Kx=RSA Au=RSA Enc=Camellia(256) Mac=SHA1
PSK-AES256-CBC-SHA SSLv3 Kx=PSK Au=PSK Enc=AES(256) Mac=SHA1
ECDHE-RSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH Au=RSA Enc=AESGCM(128) Mac=AEAD
ECDHE-ECDSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESGCM(128) Mac=AEAD
ECDHE-RSA-AES128-SHA256 TLSv1.2 Kx=ECDH Au=RSA Enc=AES(128) Mac=SHA256
ECDHE-ECDSA-AES128-SHA256 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AES(128) Mac=SHA256
ECDHE-RSA-AES128-SHA SSLv3 Kx=ECDH Au=RSA Enc=AES(128) Mac=SHA1
ECDHE-ECDSA-AES128-SHA SSLv3 Kx=ECDH Au=ECDSA Enc=AES(128) Mac=SHA1
DH-DSS-AES128-GCM-SHA256 TLSv1.2 Kx=DH/DSS Au=DH Enc=AESGCM(128) Mac=AEAD
DHE-DSS-AES128-GCM-SHA256 TLSv1.2 Kx=DH Au=DSS Enc=AESGCM(128) Mac=AEAD
DH-RSA-AES128-GCM-SHA256 TLSv1.2 Kx=DH/RSA Au=DH Enc=AESGCM(128) Mac=AEAD
DHE-RSA-AES128-GCM-SHA256 TLSv1.2 Kx=DH Au=RSA Enc=AESGCM(128) Mac=AEAD
DHE-RSA-AES128-SHA256 TLSv1.2 Kx=DH Au=RSA Enc=AES(128) Mac=SHA256
DHE-DSS-AES128-SHA256 TLSv1.2 Kx=DH Au=DSS Enc=AES(128) Mac=SHA256
DH-RSA-AES128-SHA256 TLSv1.2 Kx=DH/RSA Au=DH Enc=AES(128) Mac=SHA256
DH-DSS-AES128-SHA256 TLSv1.2 Kx=DH/DSS Au=DH Enc=AES(128) Mac=SHA256
DHE-RSA-AES128-SHA SSLv3 Kx=DH Au=RSA Enc=AES(128) Mac=SHA1
DHE-DSS-AES128-SHA SSLv3 Kx=DH Au=DSS Enc=AES(128) Mac=SHA1
DH-RSA-AES128-SHA SSLv3 Kx=DH/RSA Au=DH Enc=AES(128) Mac=SHA1
DH-DSS-AES128-SHA SSLv3 Kx=DH/DSS Au=DH Enc=AES(128) Mac=SHA1
DHE-RSA-SEED-SHA SSLv3 Kx=DH Au=RSA Enc=SEED(128) Mac=SHA1
DHE-DSS-SEED-SHA SSLv3 Kx=DH Au=DSS Enc=SEED(128) Mac=SHA1
DH-RSA-SEED-SHA SSLv3 Kx=DH/RSA Au=DH Enc=SEED(128) Mac=SHA1
DH-DSS-SEED-SHA SSLv3 Kx=DH/DSS Au=DH Enc=SEED(128) Mac=SHA1
DHE-RSA-CAMELLIA128-SHA SSLv3 Kx=DH Au=RSA Enc=Camellia(128) Mac=SHA1
DHE-DSS-CAMELLIA128-SHA SSLv3 Kx=DH Au=DSS Enc=Camellia(128) Mac=SHA1
DH-RSA-CAMELLIA128-SHA SSLv3 Kx=DH/RSA Au=DH Enc=Camellia(128) Mac=SHA1
DH-DSS-CAMELLIA128-SHA SSLv3 Kx=DH/DSS Au=DH Enc=Camellia(128) Mac=SHA1
ECDH-RSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH/RSA Au=ECDH Enc=AESGCM(128) Mac=AEAD
ECDH-ECDSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH/ECDSA Au=ECDH Enc=AESGCM(128) Mac=AEAD
ECDH-RSA-AES128-SHA256 TLSv1.2 Kx=ECDH/RSA Au=ECDH Enc=AES(128) Mac=SHA256
ECDH-ECDSA-AES128-SHA256 TLSv1.2 Kx=ECDH/ECDSA Au=ECDH Enc=AES(128) Mac=SHA256
ECDH-RSA-AES128-SHA SSLv3 Kx=ECDH/RSA Au=ECDH Enc=AES(128) Mac=SHA1
ECDH-ECDSA-AES128-SHA SSLv3 Kx=ECDH/ECDSA Au=ECDH Enc=AES(128) Mac=SHA1
AES128-GCM-SHA256 TLSv1.2 Kx=RSA Au=RSA Enc=AESGCM(128) Mac=AEAD
AES128-SHA256 TLSv1.2 Kx=RSA Au=RSA Enc=AES(128) Mac=SHA256
AES128-SHA SSLv3 Kx=RSA Au=RSA Enc=AES(128) Mac=SHA1
SEED-SHA SSLv3 Kx=RSA Au=RSA Enc=SEED(128) Mac=SHA1
CAMELLIA128-SHA SSLv3 Kx=RSA Au=RSA Enc=Camellia(128) Mac=SHA1
PSK-AES128-CBC-SHA SSLv3 Kx=PSK Au=PSK Enc=AES(128) Mac=SHA1
ECDHE-RSA-DES-CBC3-SHA SSLv3 Kx=ECDH Au=RSA Enc=3DES(168) Mac=SHA1
ECDHE-ECDSA-DES-CBC3-SHA SSLv3 Kx=ECDH Au=ECDSA Enc=3DES(168) Mac=SHA1
EDH-RSA-DES-CBC3-SHA SSLv3 Kx=DH Au=RSA Enc=3DES(168) Mac=SHA1
EDH-DSS-DES-CBC3-SHA SSLv3 Kx=DH Au=DSS Enc=3DES(168) Mac=SHA1
DH-RSA-DES-CBC3-SHA SSLv3 Kx=DH/RSA Au=DH Enc=3DES(168) Mac=SHA1
DH-DSS-DES-CBC3-SHA SSLv3 Kx=DH/DSS Au=DH Enc=3DES(168) Mac=SHA1
ECDH-RSA-DES-CBC3-SHA SSLv3 Kx=ECDH/RSA Au=ECDH Enc=3DES(168) Mac=SHA1
ECDH-ECDSA-DES-CBC3-SHA SSLv3 Kx=ECDH/ECDSA Au=ECDH Enc=3DES(168) Mac=SHA1
DES-CBC3-SHA SSLv3 Kx=RSA Au=RSA Enc=3DES(168) Mac=SHA1
IDEA-CBC-SHA SSLv3 Kx=RSA Au=RSA Enc=IDEA(128) Mac=SHA1
PSK-3DES-EDE-CBC-SHA SSLv3 Kx=PSK Au=PSK Enc=3DES(168) Mac=SHA1
KRB5-IDEA-CBC-SHA SSLv3 Kx=KRB5 Au=KRB5 Enc=IDEA(128) Mac=SHA1
KRB5-DES-CBC3-SHA SSLv3 Kx=KRB5 Au=KRB5 Enc=3DES(168) Mac=SHA1
KRB5-IDEA-CBC-MD5 SSLv3 Kx=KRB5 Au=KRB5 Enc=IDEA(128) Mac=MD5
KRB5-DES-CBC3-MD5 SSLv3 Kx=KRB5 Au=KRB5 Enc=3DES(168) Mac=MD5
ECDHE-RSA-RC4-SHA SSLv3 Kx=ECDH Au=RSA Enc=RC4(128) Mac=SHA1
ECDHE-ECDSA-RC4-SHA SSLv3 Kx=ECDH Au=ECDSA Enc=RC4(128) Mac=SHA1
ECDH-RSA-RC4-SHA SSLv3 Kx=ECDH/RSA Au=ECDH Enc=RC4(128) Mac=SHA1
ECDH-ECDSA-RC4-SHA SSLv3 Kx=ECDH/ECDSA Au=ECDH Enc=RC4(128) Mac=SHA1
RC4-SHA SSLv3 Kx=RSA Au=RSA Enc=RC4(128) Mac=SHA1
RC4-MD5 SSLv3 Kx=RSA Au=RSA Enc=RC4(128) Mac=MD5
PSK-RC4-SHA SSLv3 Kx=PSK Au=PSK Enc=RC4(128) Mac=SHA1
KRB5-RC4-SHA SSLv3 Kx=KRB5 Au=KRB5 Enc=RC4(128) Mac=SHA1
KRB5-RC4-MD5 SSLv3 Kx=KRB5 Au=KRB5 Enc=RC4(128) Mac=MD5
CentOS 8.x 上面自带的 OpenSSL 版本是 OpenSSL 1.1.1g FIPS 21 Apr 2020, 检测支持加密套件 openssl ciphers -v,返回信息如下:
TLS_AES_256_GCM_SHA384 TLSv1.3 Kx=any Au=any Enc=AESGCM(256) Mac=AEAD
TLS_CHACHA20_POLY1305_SHA256 TLSv1.3 Kx=any Au=any Enc=CHACHA20/POLY1305(256) Mac=AEAD
TLS_AES_128_GCM_SHA256 TLSv1.3 Kx=any Au=any Enc=AESGCM(128) Mac=AEAD
TLS_AES_128_CCM_SHA256 TLSv1.3 Kx=any Au=any Enc=AESCCM(128) Mac=AEAD
ECDHE-ECDSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESGCM(256) Mac=AEAD
ECDHE-RSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH Au=RSA Enc=AESGCM(256) Mac=AEAD
ECDHE-ECDSA-CHACHA20-POLY1305 TLSv1.2 Kx=ECDH Au=ECDSA Enc=CHACHA20/POLY1305(256) Mac=AEAD
ECDHE-RSA-CHACHA20-POLY1305 TLSv1.2 Kx=ECDH Au=RSA Enc=CHACHA20/POLY1305(256) Mac=AEAD
ECDHE-ECDSA-AES256-CCM TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESCCM(256) Mac=AEAD
ECDHE-ECDSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESGCM(128) Mac=AEAD
ECDHE-RSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH Au=RSA Enc=AESGCM(128) Mac=AEAD
ECDHE-ECDSA-AES128-CCM TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESCCM(128) Mac=AEAD
ECDHE-ECDSA-AES128-SHA256 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AES(128) Mac=SHA256
ECDHE-RSA-AES128-SHA256 TLSv1.2 Kx=ECDH Au=RSA Enc=AES(128) Mac=SHA256
ECDHE-ECDSA-AES256-SHA TLSv1 Kx=ECDH Au=ECDSA Enc=AES(256) Mac=SHA1
ECDHE-RSA-AES256-SHA TLSv1 Kx=ECDH Au=RSA Enc=AES(256) Mac=SHA1
ECDHE-ECDSA-AES128-SHA TLSv1 Kx=ECDH Au=ECDSA Enc=AES(128) Mac=SHA1
ECDHE-RSA-AES128-SHA TLSv1 Kx=ECDH Au=RSA Enc=AES(128) Mac=SHA1
AES256-GCM-SHA384 TLSv1.2 Kx=RSA Au=RSA Enc=AESGCM(256) Mac=AEAD
AES256-CCM TLSv1.2 Kx=RSA Au=RSA Enc=AESCCM(256) Mac=AEAD
AES128-GCM-SHA256 TLSv1.2 Kx=RSA Au=RSA Enc=AESGCM(128) Mac=AEAD
AES128-CCM TLSv1.2 Kx=RSA Au=RSA Enc=AESCCM(128) Mac=AEAD
AES256-SHA256 TLSv1.2 Kx=RSA Au=RSA Enc=AES(256) Mac=SHA256
AES128-SHA256 TLSv1.2 Kx=RSA Au=RSA Enc=AES(128) Mac=SHA256
AES256-SHA SSLv3 Kx=RSA Au=RSA Enc=AES(256) Mac=SHA1
AES128-SHA SSLv3 Kx=RSA Au=RSA Enc=AES(128) Mac=SHA1
DHE-RSA-AES256-GCM-SHA384 TLSv1.2 Kx=DH Au=RSA Enc=AESGCM(256) Mac=AEAD
DHE-RSA-CHACHA20-POLY1305 TLSv1.2 Kx=DH Au=RSA Enc=CHACHA20/POLY1305(256) Mac=AEAD
DHE-RSA-AES256-CCM TLSv1.2 Kx=DH Au=RSA Enc=AESCCM(256) Mac=AEAD
DHE-RSA-AES128-GCM-SHA256 TLSv1.2 Kx=DH Au=RSA Enc=AESGCM(128) Mac=AEAD
DHE-RSA-AES128-CCM TLSv1.2 Kx=DH Au=RSA Enc=AESCCM(128) Mac=AEAD
DHE-RSA-AES256-SHA256 TLSv1.2 Kx=DH Au=RSA Enc=AES(256) Mac=SHA256
DHE-RSA-AES128-SHA256 TLSv1.2 Kx=DH Au=RSA Enc=AES(128) Mac=SHA256
DHE-RSA-AES256-SHA SSLv3 Kx=DH Au=RSA Enc=AES(256) Mac=SHA1
DHE-RSA-AES128-SHA SSLv3 Kx=DH Au=RSA Enc=AES(128) Mac=SHA1
PSK-AES256-GCM-SHA384 TLSv1.2 Kx=PSK Au=PSK Enc=AESGCM(256) Mac=AEAD
PSK-CHACHA20-POLY1305 TLSv1.2 Kx=PSK Au=PSK Enc=CHACHA20/POLY1305(256) Mac=AEAD
PSK-AES256-CCM TLSv1.2 Kx=PSK Au=PSK Enc=AESCCM(256) Mac=AEAD
PSK-AES128-GCM-SHA256 TLSv1.2 Kx=PSK Au=PSK Enc=AESGCM(128) Mac=AEAD
PSK-AES128-CCM TLSv1.2 Kx=PSK Au=PSK Enc=AESCCM(128) Mac=AEAD
PSK-AES256-CBC-SHA SSLv3 Kx=PSK Au=PSK Enc=AES(256) Mac=SHA1
PSK-AES128-CBC-SHA256 TLSv1 Kx=PSK Au=PSK Enc=AES(128) Mac=SHA256
PSK-AES128-CBC-SHA SSLv3 Kx=PSK Au=PSK Enc=AES(128) Mac=SHA1
DHE-PSK-AES256-GCM-SHA384 TLSv1.2 Kx=DHEPSK Au=PSK Enc=AESGCM(256) Mac=AEAD
DHE-PSK-CHACHA20-POLY1305 TLSv1.2 Kx=DHEPSK Au=PSK Enc=CHACHA20/POLY1305(256) Mac=AEAD
DHE-PSK-AES256-CCM TLSv1.2 Kx=DHEPSK Au=PSK Enc=AESCCM(256) Mac=AEAD
DHE-PSK-AES128-GCM-SHA256 TLSv1.2 Kx=DHEPSK Au=PSK Enc=AESGCM(128) Mac=AEAD
DHE-PSK-AES128-CCM TLSv1.2 Kx=DHEPSK Au=PSK Enc=AESCCM(128) Mac=AEAD
DHE-PSK-AES256-CBC-SHA SSLv3 Kx=DHEPSK Au=PSK Enc=AES(256) Mac=SHA1
DHE-PSK-AES128-CBC-SHA256 TLSv1 Kx=DHEPSK Au=PSK Enc=AES(128) Mac=SHA256
DHE-PSK-AES128-CBC-SHA SSLv3 Kx=DHEPSK Au=PSK Enc=AES(128) Mac=SHA1
ECDHE-PSK-CHACHA20-POLY1305 TLSv1.2 Kx=ECDHEPSK Au=PSK Enc=CHACHA20/POLY1305(256) Mac=AEAD
ECDHE-PSK-AES256-CBC-SHA TLSv1 Kx=ECDHEPSK Au=PSK Enc=AES(256) Mac=SHA1
ECDHE-PSK-AES128-CBC-SHA256 TLSv1 Kx=ECDHEPSK Au=PSK Enc=AES(128) Mac=SHA256
ECDHE-PSK-AES128-CBC-SHA TLSv1 Kx=ECDHEPSK Au=PSK Enc=AES(128) Mac=SHA1
除非重新编译 OpenSSL 加入 enable-weak-ssl-ciphers 参数,开启对 TLSv1/SSLv3 with ECDHE-RSA-AES128-GCM-SHA256, 128 secret bits cipher 的支持,但是 这里有个大坑,尝试降级时把服务器搞宕机了2次,OpenSSH 依赖 OpenSSL,升级时会破坏依赖,当前已经打开的 SSH 终端会话 可以保持连接一段时间,随时会暴毙,后续新开的 SHH 会话全部会失败,因为 SSH 在升级完 OpenSSL 就已经挂了,执行 ssh -V 输出 ssh: symbol lookup error: /lib64/libk5crypto.so.3: undefined symbol: EVP_KDF_ctrl, version OPENSSL_1_1_1b
下载这个 RPM 包:
http://mirror.centos.org/centos/8/BaseOS/x86_64/os/Packages/openssl-libs-1.1.1g-15.el8_3.x86_64.rpm
提取依赖的旧版本库文件,然后传到服务端,放到相关路径并把 OpenSSH 的依赖 软连接提取到的库文件。具体可以参考这个链接:
https://blog.csdn.net/hzcm1984/article/details/115958795
修复依赖时要手速,抢在 SSH 挂掉前弄好,不然到时候 VNC 也是一起炸的,与服务器彻底失联,得新开一台临时服务器挂盘取回数据(别问我怎么知道,欲语泪先流)。

3 条评论
就跟 SMTP 发件加密端口一样, SSL 465 是Implicit TLS,同样也是面临 ftps 类似困境, 465 端口并没有得到标准的实现,仅仅是约定俗成的(没正式提交给 RFC),而 587 为 TLS 端口,是被标准化了,也的确是默认端口,587 类似 ftps 的 Explicit 方式,先明文协商,根据协商结果升级为 TLS 或降级为 明文不加密模式,而 465 全程加密
端口 465 已在 IANA 中注册,服务描述为smtps。然而,因为它只是通过 IANA 注册,并没有作为 RFC 提交给 IETF,所以它从未被完全确认为为 SMTP 的加密端口。同年,IETF 将端口 587 上的 StartTLS 标准化为 SMTP 消息提交的加密协议。
为了简化加密 SMTP 消息的过程,端口 465 和smtps已从 IANA 注册表中删除。这导致了相当多的混乱,因为端口 465 和隐式 TLS已经获得了很大的关注。为了解决这个问题,IETF 发布了一项一次性修正案,以恢复用于通过 TLS 协议提交消息的端口 465。
今天,465 端口仍然作为消息提交的服务端口和 SSM 的 URL Rendezvous Directory,简称URD列在IANA注册表中。然而,为端口 465 列出的这两个服务增加了端口的混乱,因为 URD 与 SMTP 无关。
唯一幸运的是,465 获得很大关注,大量邮件服务端进行了支持,成为了事实标准的一部分,并且与 587 同时并行,但是微软很倔,直接摆烂,就是只 支持 587,极少个别一些邮件 项目 也是这样。
请问下作者大大是如何认为隐式 FTPS 被 IETF 弃用了呢?我在RFC文档中并没有看到所谓不再支持隐式FTPS的描述。
链接不是给了?也没失效啊?怎么还会这么问,且 RFC4217 已经规范了 FTPS,有且只有 Explicit 这种方式了,Implicit 在草案阶段过去后被放弃支持了,在草案 draft-murray-auth-ftp-tls-16.txt 之后,只有 Explicit 这种方式,且最终通过 RFC 正式实施了,如果因网络不好无法访问,建议自行准备高质量梯子,不过此次我也把相关原话引用到内容去了
Why are they bad ?
From draft-murray-auth-ftp-ssl-07.txt
A. Deprecated SSL negotiation mechanisms